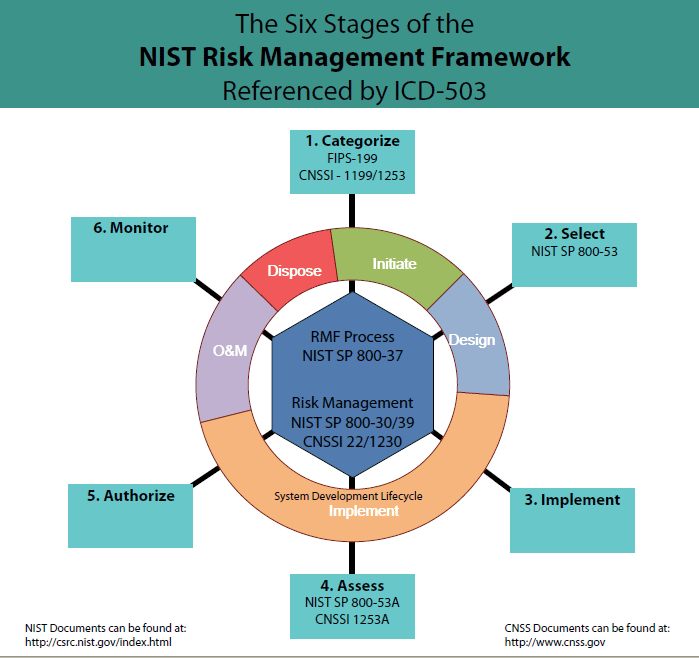
• Information system categorization
• Selection of security control
• Implementation of the security controls
• Assessing the stability of the security controls
• Authorization of information system
• Monitoring the state of the security control
Risk management helps in reducing risks an organization’s encounters in fulfillment of their business objectives and goals. RMF makes it possible to integrate security in the various stages of system development life cycle (SDLC) changing the manner in which information assurance and cyber security is done in the following ways:
1. Authorization assessment
RMF system has eliminated the Interim Authority to Operate (IATO) for any organization. This reorganization has increased the security level and you will be eliminating the possible accreditation loophole. People who are familiar versions of RMF were familiar with the long process they had to undergo in performing simple tasks such as connecting their system to the LAN for a testing period that may last up to 3 months. RMF gets rid of IATO and a system in action will standby on an Interim Authorization to Test (IATT) during the system’s testing period until it is ready for use.
RMF joins up into the ongoing security undertaking in your organization as opposed to focusing on the paperwork. The system is put under constant monitoring and evaluation to uncover any security weakness present with the period which is a shift from the usual three year special accreditation process which very efficient and saves you money. Basically, RMF changes the Certification & Accreditation (C&A) to Assessment & Authorization (A&A).
2. Common Vocabulary List
In the past, the various departments in the federal government and agencies within the international intelligence community have been using different words to mean the same description which was often confusing especially to agents from different sources in an attempt to work together. Their respective handlers faced a challenging time in the translation of one vocabulary to the next back and forth. This mostly led to errors such as a small mix in translation and in the end compromising the information security. However, this has since changed since the adoption of RMF; the system framework has facilitated agency inter-connectivity by inclusion of common lists of vocabulary.
3. A Single Regulated Process
You will need to go through limited documentation processes with RMF. This happens due to the fact that the whole Federal Government and the rest of the intelligence community has adapted this single risk management process. Information Assurance risk involved is on the minimal as the security state is heightened due to the less documentation and emphasis being put on attaining the real results.
RMF technique used in risk management is as per the 9 step guideline of NIST process from SP 800-30 which is proven to be true. Online tools such as eMassand theKnowledge Service (CAC required) are incorporated to improve the RMF roles in cynersecurity. The single centered risk management system has led to enhanced security in information assurance preventing rival attacks and threats.
4. Improved System Sectioning and Integration
The goals that almost all organizations offering cyber security aim to achieve are: confidentiality, integrity, and availability. The security of a system is strongest when it is included in the system whole the same is still under development. However, the high costs cited have seen several people shying away from this and creating and executing a system without any form of security integration. Security consideration should be on top of your list when you settle to developing any kind of system. Previously, systems were grouped using Mission Assurance Category (MAC) and Confidentiality Level (CL). The CL as the acronym suggests mapped out to the business or organization’s confidentiality and Mac category is applied in the following areas integrity and availability.
Most people will probably advise you to evade the expenses of including security factors in your system just when it is in its first cycle of development. Even though this may seem as a great alternative, your system’s security is at risk and may lead to rival attacks. RMF implements a system that meets the three information security objectives and at the same time, integrating within the Systems Development Life Cycle (SDLC) meeting the needs of the system.
5. Standard Control Set
DODI 8500.2 was in the past used by the federal government as a control when implementing the previous version of RMF – DIACAP. RMF has since shift gears in information assurance moving to the NIST SP 800-53 Revision 4 control created to correspond to the controls that are in use withing the entire Federal government and intelligence community. These two control sets are distinctively different as they were developed by two entirely different teams at different points in time. This may sound stressful and confusing on how to shift from one control set to the next, nonetheless,
RMF control set NIST is structure and easier to work with. No need to worry if you were conversant with the previous version of the control set as the federal government through DoD have developed a matrix that illustrates the controls matching to the current RMF controls which can easily be accessed via the online tool- Knowledge Service (CAC required) and updating all control manuals.








Leave a Reply